White Hat Operation: Ronin Network’s $10M ETH Recovery Explained
The Ronin Network, a key player in the gaming blockchain sector and the backbone of the popular play-to-earn game Axie Infinity, recently faced a significant security breach. This breach resulted in the loss of approximately $9.8 million worth of Ether (ETH). Initially perceived as a malicious attack, recent developments suggest it might have been an accidental operation by a white hat hacker, who has since agreed to return the stolen funds. As of now, the hacker has returned 3,991 ETH.
Was the Ronin Exploit Just an Accidental White Hat Operation?
White hat hackers typically identify and exploit vulnerabilities to expose security flaws, helping to fix the issues and then returning any stolen assets. An update from PeckShield on August 6 suggested that such an ethical hacker might have carried out the exploit on Ronin Network.
This exploit involved a maximal extractable value (MEV) bot, a tool used by validators to find arbitrage opportunities across decentralized finance (DeFi) platforms.
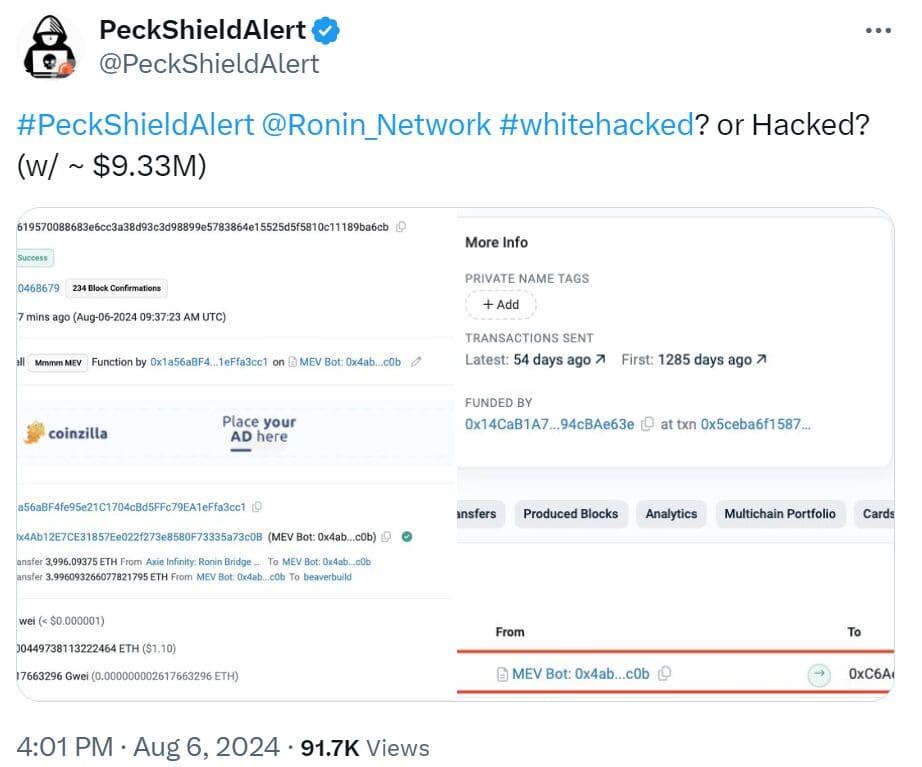
These bots automatically implement strategies to capitalize on market price differences. In this instance, the transaction was executed by an MEV bot identified as “0x4ab,” which then transferred 3.9 ETH to a wallet known as “0x952” or “beaver build.”
From Breach to Resolution: The Return of the Funds
Ronin Network confirmed that approximately 4,000 ETH and 2 million USDC were withdrawn—the maximum amounts that could be taken out in a single transaction. The Axie Infinity contract deployer publicly thanked the hacker for safeguarding user funds and initiated communication via Blockscan chat.
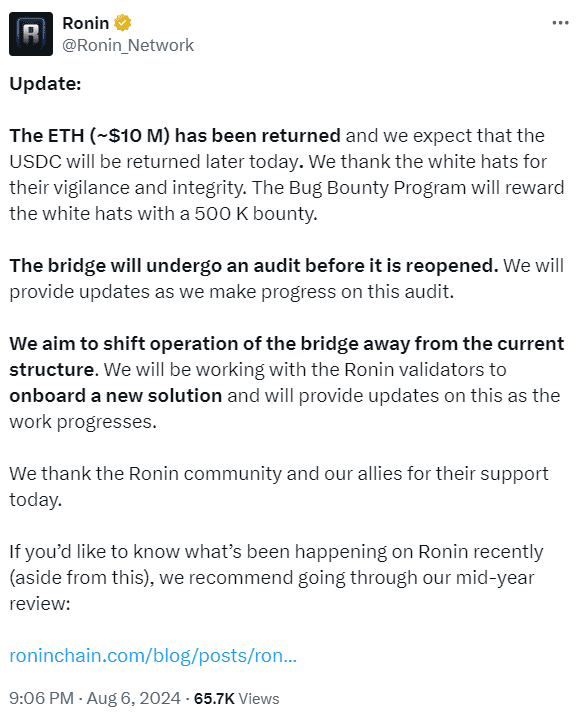
This communication led to the full return of all ETH and the anticipated return of all USDC. At the time the ETH was returned, it was worth over $10 million. The bot may have unintentionally front-run the attack, leading to the breach.
Ronin Network’s Response and Future Measures
According to data from Etherscan, the MEV bot that drained the funds returned nearly all of them. A total of 3,991 ETH was transferred back to the Ronin team at 3:04 pm UTC, with only 5 ETH remaining unreturned. As a goodwill gesture, the Ronin team rewarded the MEV bot owner $500,000 for discovering the exploit.
The Ronin team explained that a recent bridge upgrade, deployed via its governance process, introduced an issue causing the bridge to misinterpret the required vote threshold for fund withdrawals. They are now working on a solution, with plans for a new bridge upgrade to undergo intensive audits before deployment.
Historical Context and Broader Implications
This incident adds to Ronin’s history of security breaches. Late last year, the Ronin Bridge was hacked for over $600 million in one of the largest crypto heists to date. The broader implications of this incident extend to the entire cryptocurrency sector, which has seen a worrying increase in hacks in 2024.
The first quarter alone reported $542.7 million stolen—a 42% rise from the same period in 2023. July was particularly devastating, with over $266 million worth of crypto hacks across 16 incidents, including the $234 million theft from WazirX.




